John The Ripper
Task 1
Read all that is in the task and press on complete
Task 2
2.1 What is the most popular extended version of John the Ripper?
Answer: Jumbo John
Task 3
What website was the rockyou.txt wordlist created from a breach on?
Answer: rockyou.com
Task 4
Download the file attached to this task
4.1 What type of hash is hash1.txt?
Hash Type Identifier – Identify unknown hashes or use hash-id command
Answer: MD5
4.2 What is the cracked value of hash1.txt?
john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt hash1.txt
4.3 What type of hash is hash2.txt?
Hash Type Identifier – Identify unknown hashes or use hash-id command
Answer: Sha1
4.4 What is the cracked value of hash2.txt
john --format=raw-sha1 --wordlist=/usr/share/wordlists/rockyou.txt hash2.txt
4.5 What type of hash is hash3.txt?
Hash Type Identifier – Identify unknown hashes or use hash-id command
Answer: sha256
4.6 What is the cracked value of hash3.txt
john --format=raw-sha256 --wordlist=/usr/share/wordlists/rockyou.txt hash3.txt
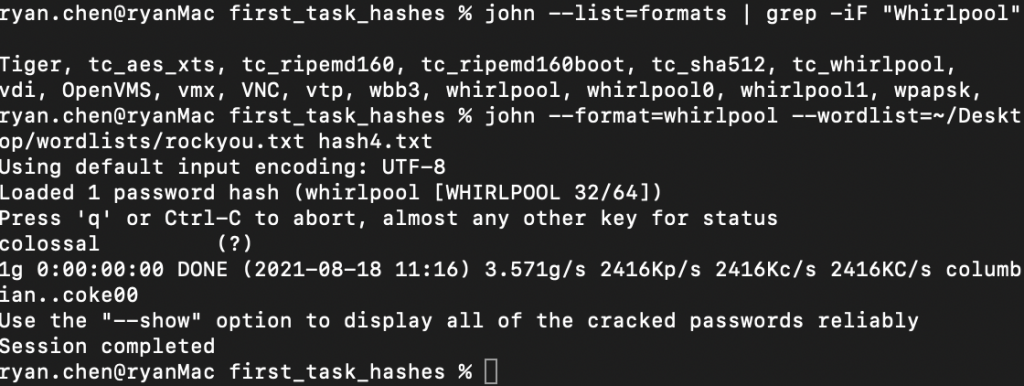
4.7 What type of hash is hash4.txt?
Hash Type Identifier – Identify unknown hashes or use hash-id command
Answer: Whirlpool
4.8 What is the cracked value of hash4.txt?
john --format=whirlpool --wordlist=/usr/share/wordlists/rockyou.txt hash4.txt
Task 5
5.1 What do we need to set the “format” flag to, in order to crack this?
Answer: NT
5.2 What is the cracked value of this password?
john --format=nt--wordlist=/usr/share/wordlists/rockyou.txt ntlmtxt
Task 6
6.1 What is the root password?
john --wordlist=/usr/share/wordlists/rockyou.txt --format=sha512crypt etchashes.txt
Task 7
7.1 What is Joker’s password?
根據說明single模式下要添加名稱告訴john去踹密碼… 添加Joker:在hash7.txt前面
john --single --format=raw-md5 hash7.txt
Task 8
8.1 What do custom rules allow us to exploit?
Answer: Password complexity predictability
8.2 What rule would we use to add all capital letters to the end of the word?
Answer: Az"[A-Z]"
8.3 What flag would we use to call a custom rule called “THMRules”
Answer: -rule=THMRules
9.1 What is the password for the secure.zip file?
zip2john secure.zip > zip_hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt zip_hash.txt
9.2 What is the contents of the flag inside the zip file?
Answer: THM{w3ll_d0n3_h4sh_r0y4l}
Task 10
10.1 What is the password for the secure.rar file?
rar2john secure.zip > rar_hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt rar_hash.txt
10.2 What is the contents of the flag inside the zip file?
THM{r4r_4rch1ve5_th15_t1m3}
Task 11
11.1 What is the SSH private key password?
Now we need to convert the keys to a readable hash by typing
ssh2john.py idrsa.id_rsa > id.txt
john --wordlist=/usr/share/wordlists/rockyou.txt id.txt
題外話 用mac用戶brew install john時要下載 brew install john-jumbo , 踩到這個坑一度跑不出來…
在弄zip2john跟unshadow 如果用brew 安裝到mac可能會找不到command,網路上似乎也沒人解決過…所以我就寫了解法出來囉…
My mac is also Big Sur M1.
If you install john and use brew, the brew install john-jumbo command “zip2john” will be in “/opt/homebrew/Cellar/john-jumbo/1.9.0/share/john/zip2john” on the path.
Because, john only links to /opt/homebrew/bin/ So I can’t find it
Maybe you can add /opt/homebrew/Cellar/john-jumbo/1.9.0/share/john/ to $PATH ,then it can be used normally
ryan.chen@ryanMac bin % ls -al | grep "john"
lrwxr-xr-x 1 ryan.chen admin 35 Aug 18 11:05 john -> ../Cellar/john-jumbo/1.9.0/bin/john
ryan.chen@ryanMac john % ./zip2john
Usage: ./zip2john [options] [zip file(s)]
Options for 'old' PKZIP encrypted files only:
-a <filename> This is a 'known' ASCII file. This can be faster, IF all
files are larger, and you KNOW that at least one of them starts out as
'pure' ASCII data.
-o <filename> Only use this file from the .zip file.
-c This will create a 'checksum only' hash. If there are many encrypted
files in the .zip file, then this may be an option, and there will be
enough data that false possitives will not be seen. If the .zip is 2
byte checksums, and there are 3 or more of them, then we have 48 bits
knowledge, which 'may' be enough to crack the password, without having
to force the user to have the .zip file present.
-m Use "file magic" as known-plain if applicable. This can be faster but
not 100% safe in all situations.
-2 Force 2 byte checksum computation.
NOTE: By default it is assumed that all files in each archive have the same
password. If that's not the case, the produced hash may be uncrackable.
To avoid this, use -o option to pick a file at a time.
ryan.chen@ryanMac john % pwd
/opt/homebrew/Cellar/john-jumbo/1.9.0/share/john