結構化威脅資訊表達式 (Structured Threat Information eXpression, STIX)[1]是一種用於交換網路威脅情報(CTI)的語言。
想了很久,想說直接講威脅情資平台再來分析資料,後來決定要從資料交換說起。
例如某個 IoC 來自某個駭客組織的關係圖如下
indicatres
Indicator -------------> Threat Actor我們可以從文件[2]看到 indicator 解釋
Indicator作為來源,它的關係會是indicates,有向圖連結的目標有可能是attack-pattern, canpaign, infrastructure, intrusion-set, malware, threat-actor, tool
這可以描述 IoC 可以檢測到相關攻擊(上面列的)的證據。
對象(Objects)
STIX 針對每個對象或稱物件定義了一些分類,稱作 SDO,分別如下:
- Attack Pattern
- Campaign
- Course of Action
- Grouping
- Identity
- Indicator
- Infrastructure
- Intrusion Set
- Location
- Malware
- Malware Analysis
- Note
- Observed Data
- Report
- Opinion
- Threat Actor
- Tool
- Vulnerability
使用 STIX 可以很容易看出對象跟描述之間的關係。
關係物件
有了 SDO 作為節點,描述關係對象稱作 SRO,有兩類:
- Relationship
- Sighting
範例
我們用 github (https://oasis-open.github.io/cti-documentation/examples/identifying-a-threat-actor-profile)提供的範例來說明
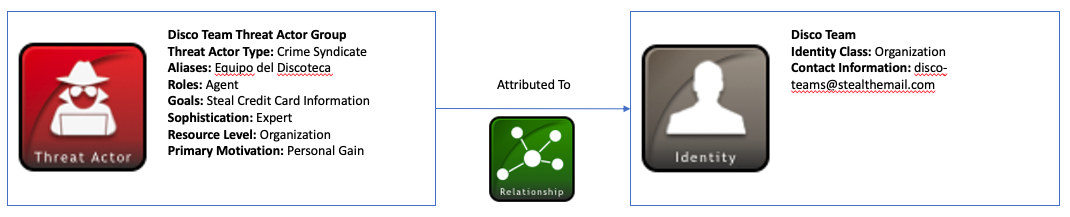
結構化的資料可以表示為
{
"type": "bundle",
"id": "bundle--601cee35-6b16-4e68-a3e7-9ec7d755b4c3",
"objects": [
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--dfaa8d77-07e2-4e28-b2c8-92e9f7b04428",
"created": "2014-11-19T23:39:03.893Z",
"modified": "2014-11-19T23:39:03.893Z",
"name": "Disco Team Threat Actor Group",
"description": "This organized threat actor group operates to create profit from all types of crime.",
"threat_actor_types": [
"crime-syndicate"
],
"aliases": [
"Equipo del Discoteca"
],
"roles": [
"agent"
],
"goals": [
"Steal Credit Card Information"
],
"sophistication": "expert",
"resource_level": "organization",
"primary_motivation": "personal-gain"
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--733c5838-34d9-4fbf-949c-62aba761184c",
"created": "2016-08-23T18:05:49.307Z",
"modified": "2016-08-23T18:05:49.307Z",
"name": "Disco Team",
"description": "Disco Team is the name of an organized threat actor crime-syndicate.",
"identity_class": "organization",
"contact_information": "disco-team@stealthemail.com"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a2e3efb5-351d-4d46-97a0-6897ee7c77a0",
"created": "2020-02-29T18:01:28.577Z",
"modified": "2020-02-29T18:01:28.577Z",
"relationship_type": "attributed-to",
"source_ref": "threat-actor--dfaa8d77-07e2-4e28-b2c8-92e9f7b04428",
"target_ref": "identity--733c5838-34d9-4fbf-949c-62aba761184c"
}
]
}下一步我們把該檔案的程式碼貼在 https://oasis-open.github.io/cti-stix-visualization/
可以看到他們之間的關係
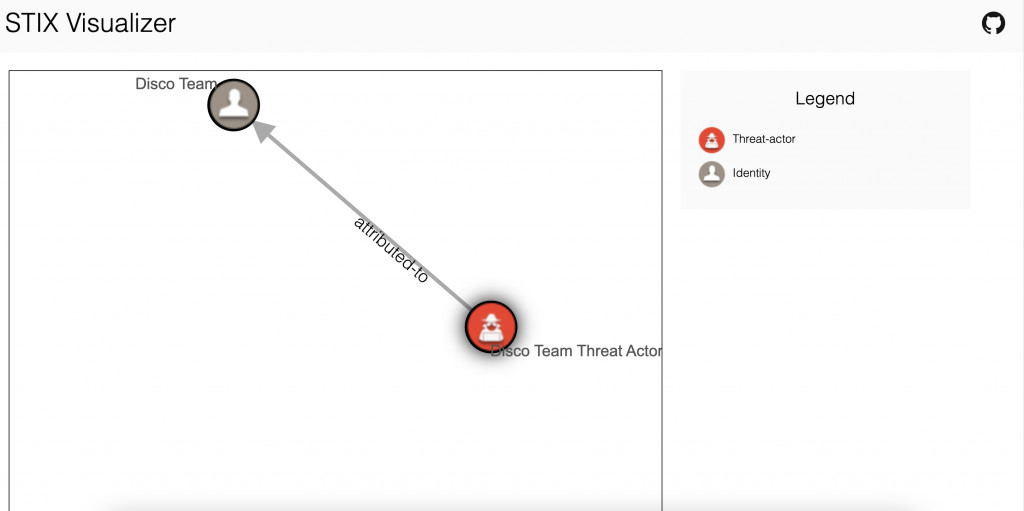
這樣有點沒意思,我們拿真實資料試試,到 alienvault 這個開源情資共享平台抓一些最近的情資.
先到 https://otx.alienvault.com/browse/global/pulses
他們對新的情資稱作脈衝(Pulses) 有很多情資共享平台都會抓取這個平台的資料,
每天都會有的情資比較像是 Honeypot (蜜罐) 偵測到的資料,
或是一些資安設備捕捉到惡意的流量轉換成 IoC,
所以這邊挑一個比較有故事性的。
比如我在右上方搜尋 「APT 41」,我們看到一則蠻有趣的情資…請參考 Reference 3 或這個連結 https://otx.alienvault.com/pulse/630615f326d4b91e473170fe
In March 2022 one of the oldest state-sponsored hacker groups, APT41, breached government networks in six US states, including by exploiting a vulnerability in a livestock management system, Mandiant investigators have reported.[3]點擊右上方 Download 記得選 STIX 2.1
打開後大概長這樣(截入一小段 code)
{
"id": "bundle--44717e74-05e2-4c27-935e-bb67b7227d2d",
"objects": [
{
"created": "2022-08-24T12:13:38.777Z",
"created_by_ref": "identity--ab072f15-9b87-4ee1-898f-b584d41f29b0",
"description": "In March 2022 one of the oldest state-sponsored hacker groups, APT41, breached government networks in six US states, including by exploiting a vulnerability in a livestock management system, Mandiant investigators have reported.",
"id": "report--44717e74-05e2-4c27-935e-bb67b7227d2d",
"labels": [
"threat-report"
],
"modified": "2022-08-24T12:13:38.777Z",
"name": "APT41 World Tour 2021 on a tight schedule",
"object_refs": [
"identity--ab072f15-9b87-4ee1-898f-b584d41f29b0",
.......我們就會看到這個 APT41 參考到非常多 hashes.MD5
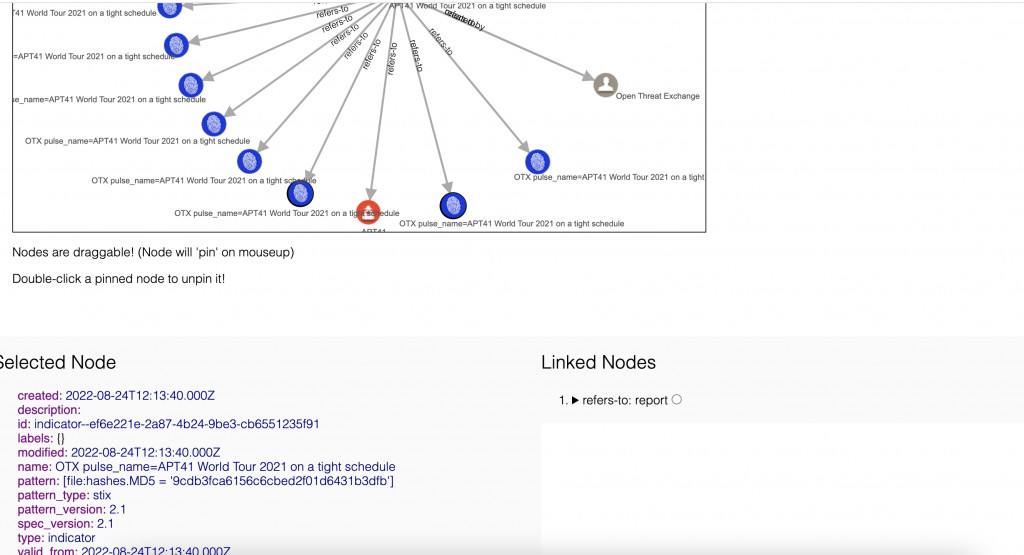
注意上面雖然都是寫 OTX pulse_name …,但是圖案是代表 indicator 的意思,這其實是解析的問題,就像是我從 I-SAC 匯出的情資丟到 MISP 上格式雖然走 STIX 2.0 但還是會跑掉…,這時候就需要在 MISP 上開發新的轉換器。
小節
今天說明威脅情資的交換格式,明天來討論自動情報資訊交換(TAXII)。
另外可視化介面一直都是最終呈現給用戶最好的呈現方式…,看圖說故事比用文字描述好吧我想。
更多補充內容可以到 https://SecTools.tw 尋找。
Reference
[1] Sharing threat intelligence just got a lot easier!. https://oasis-open.github.io/cti-documentation/
[2] STIX2.1 OASIS Standard https://docs.oasis-open.org/cti/stix/v2.1/os/stix-v2.1-os.html#_e2e1szrqfoan
[3] APT41 World Tour 2021. https://otx.alienvault.com/pulse/630615f326d4b91e473170fe
此文也發布在 Ithome 鐵人賽中。